
The Transformation of the 3LoD Model into an Advanced Persistent Defense
Itay Yamin
Nov 21, 2024
The Three Lines of Defense (3LoD) model, while often associated with cybersecurity and risk management, is fundamentally about improving how organizations handle risk at all levels. It enables effective information flow between organization functions, ensures clarity in roles, and highlights areas where independence is critical for a clearer view of risks. Despite the term "defense," the 3LoD model is not just about technical controls or defense-in-depth strategies. Instead, it is a governance and management framework designed to strengthen accountability and collaboration. This distinction is vital for understanding the model's focus: building a cohesive, strategic approach to managing organizational risk – Advanced Persistent Defense Approach.
Here’s a quick recap of the three lines:
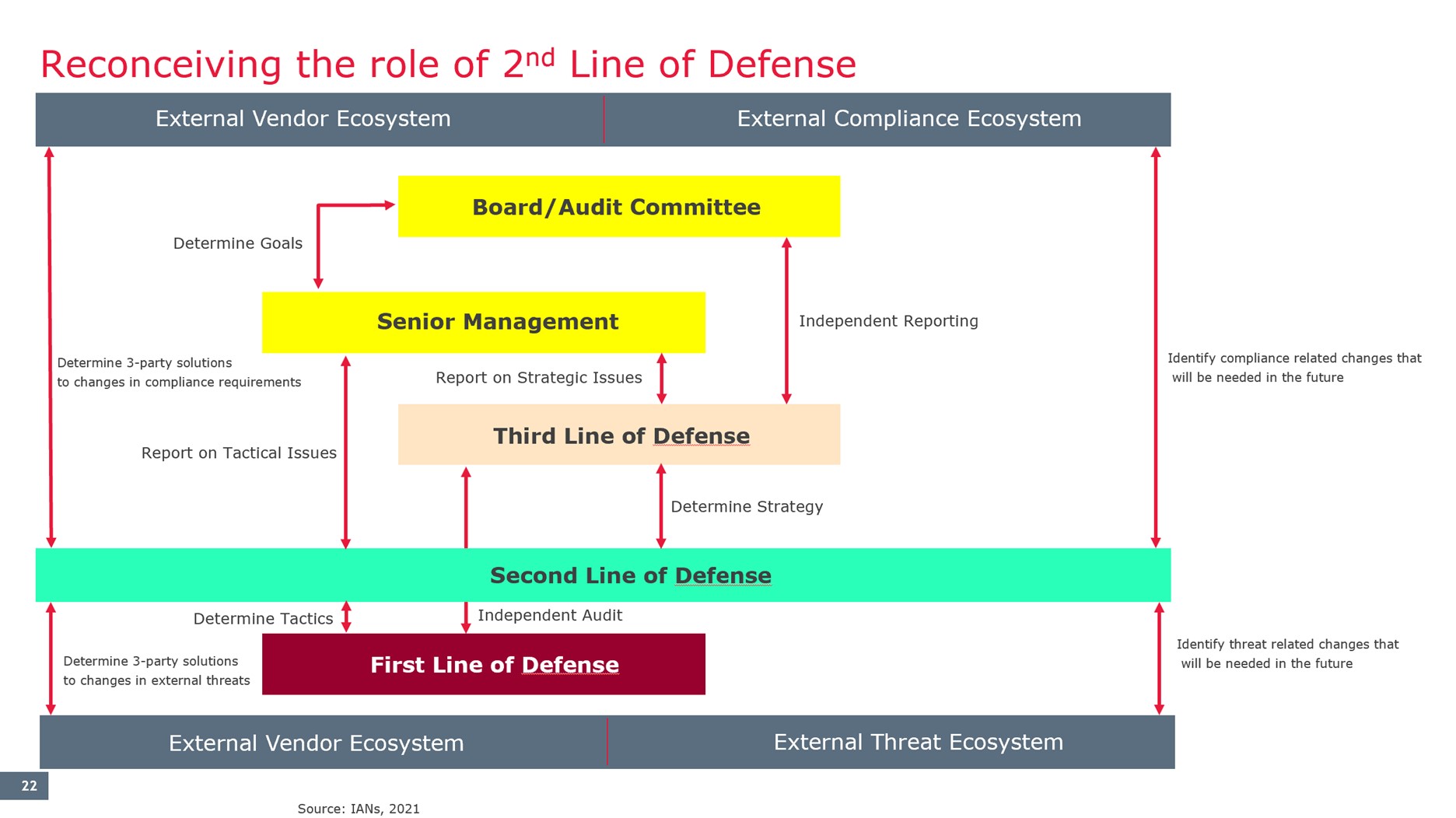
1. First Line of Defense (1LoD): Operational Management
The first line is responsible for managing day-to-day risks within operational activities. This includes identifying, assessing, and mitigating risks directly within their processes. Operational managers and staff are tasked with implementing risk controls and are closest to the organization's core operations.
2. Second Line of Defense (2LoD): Risk Management and Compliance
The second line oversees and supports the first line by establishing policies, frameworks, and compliance guidelines. It ensures that risk controls are effective and aligned with organizational risk appetite and regulatory requirements. The 2LoD acts as a bridge between operational risk management and strategic oversight.
3. Third Line of Defense (3LoD): Internal Audit
The third line provides independent assurance by evaluating the effectiveness of risk management practices. Internal auditors assess how well risks are being managed and whether controls are robust and aligned with strategic goals.
Why Transform the 3LoD Model?
As organizations embrace digital transformation, the traditional 3LoD model has evolved to meet the demands of modern, interconnected ecosystems. The transformation is particularly evident in the expanded role of the 2LoD, which now serves as a strategic partner with a deep understanding of business operations, orchestrating an advanced persistent defense against emerging threats.
This evolution reflects the challenges posed by technological advancements over the past 15 years:
1. The Rise of Data-Driven Experiences
Customer demand for enriched, data-centric services has grown exponentially. Organizations now process large volumes of structured and unstructured data from interconnected third-party sources in near real time.
2. Migration to Cloud and Hybrid Environments
To scale and adapt, many organizations have shifted from on-premises systems to cloud or hybrid infrastructures. This shift allows for greater flexibility and operational agility but introduces new vulnerabilities.
3. The Advent of Artificial Intelligence
Organizations increasingly leverage AI, including Large Language Models (LLMs), to automate data-intensive tasks and create innovative solutions. While these technologies enable efficiency, they also lower the barriers for adversaries to exploit vulnerabilities using offensive AI.
4. Complexity in the Threat Landscape
Modern attackers exploit cloud environments, SaaS applications, and organizational silos. Poor communication among teams and overlooked basic security principles create fertile ground for breaches.
A Modern Security Challenge
Organizations now defend hundreds of interconnected applications that exchange sensitive data daily. Security teams face an uphill battle managing:
- Limited personnel tasked with protecting complex environments
- A deluge of false-positive alerts, which hampers their ability to identify and prioritize actual risks
- Sophisticated threats targeting exploitable vulnerabilities across supply chains and networks
The Role of Regulators
Regulatory bodies recognize these challenges and enforce stricter compliance standards, imposing significant penalties for noncompliance. This regulatory pressure drives organizations to strengthen their security posture and invest in advanced tools like Extended Detection and Response (XDR) platforms, which leverage AI for earlier threat detection and response.
The Transformed 3LoD: An Integrated Approach
First Line of Defense (1LoD)
The 1LoD now adopts automated controls and remediation mechanisms, handling security challenges across complex third-party ecosystems. To address talent shortages, embedding security champions within development teams is critical. These champions bridge the gap between technical implementation and strategic alignment with business objectives.
Second Line of Defense (2LoD)
The 2LoD takes on a dual role: strategic navigator and advocate for the 1LoD. By aligning security risk management strategies with business goals, the 2LoD ensures that investments in defensive measures are both effective and scalable. This layer also identifies quick wins by addressing overlooked security basics, maintaining direct communication with senior leadership to steer long-term defense strategies.
Third Line of Defense (3LoD)
The 3LoD provides forward-looking assurance, leveraging predictive analytics to assess future risks. It ensures that the 2LoD's strategies are rigorously audited and aligned with organizational objectives, offering unbiased insights to the board and senior management.
Centralized and Visible Synergy
To ensure alignment across all three lines, organizations should implement centralized interfaces that offer:
- Near real-time visibility into 1LoD security metrics
- Data-driven decision-making support for the 2LoD
- Comprehensive audit capabilities for the 3LoD
These interfaces should integrate business KPIs, allowing senior leaders to provide strategic input into the organization's security posture.
The Path Forward
As organizations adapt to this transformed model, the emphasis will increasingly shift from simply enforcing cybersecurity measures to strategically aligning them with business objectives. By doing so, the Three Lines of Defense will evolve into a cohesive framework for an advanced persistent defense, capable of mitigating risks in today's dynamic threat landscape.
Interested in implementing this approach? Organizations can partner with Crimson Vista to host workshops with executive teams and boards, crafting a tailored strategy for transforming their 3LoD into a robust, advanced persistent defense framework.